Demystifying AWS Security: 8 Key Considerations for Secure Cloud Environments
Amazon Web Services (AWS) provides a robust and scalable cloud computing platform that is widely adopted by organizations, but security is a shared responsibility.
Amazon Web Services (AWS) provides a robust and scalable cloud computing platform that is widely adopted by organizations. However, with the increasing reliance on AWS services, ensuring proper security measures is crucial to protect sensitive data and maintain the integrity of cloud environments. In this article, we will demystify AWS security and discuss key considerations to establish a secure cloud environment on AWS. Before we dive into the eight points, let's quickly discuss an interesting case study that will make what we will discuss later in this article more pertinent.
Case Study: Capital One Data Breach
In 2019, Capital One experienced a significant data breach that exposed sensitive customer information. The breach affected approximately 100 million individuals in the United States and approximately 6 million in Canada, with a hacker illicitly accessing a total of about 140,000 Social Security numbers and approximately 80,000 linked bank account numbers of secured credit card customers.
The attack occurred due to a misconfiguration error at the application layer of a firewall installed by Capital One, which was further compounded by overly broad permissions set by the company. This misconfiguration allowed a former employee of a cloud service provider to gain unauthorized access to Capital One's Amazon Web Services (AWS) cloud environment. Once inside the environment, a Server-Side Request Forgery (SSRF) attack was used to access and exfiltrate customer data.
Although SSRF was not the primary factor in the breach, it has received attention due to its potential exploitation. It is important to note that this incident was not indicative of common SSRF compromises of AWS customers. The root cause of the breach was the misconfiguration of cloud resources and the overly permissive permissions granted to the attacker. This case underscores the criticality of proper configuration and access management practices in cloud environments, including AWS.
The incident at Capital One highlights the risks associated with misconfigurations and the importance of implementing robust security measures to prevent unauthorized access. It serves as a reminder that even organizations with advanced cloud security practices can be vulnerable to breaches if essential security considerations are overlooked.
To mitigate such risks, organizations should focus on implementing security best practices specific to AWS, such as strong identity and access management, secure network architecture, data encryption, comprehensive monitoring and logging, regular patch management, and disaster recovery planning. By diligently following these practices, organizations can strengthen their security posture and protect sensitive data within AWS environments.
Shared Responsibility Model
It is also worth noting that AWS stresses the importance of the shared responsibility model, which outlines the division of security responsibilities between AWS and its customers. AWS takes responsibility for securing the cloud infrastructure, including physical security, network infrastructure, and core service security, but customers are responsible for securing their applications, data, operating systems, network connections, and other components deployed on AWS services. They are expected to configure and manage access controls, secure their systems and data, encrypt sensitive information as they deem fit, implement regular backups and disaster recovery plans, and monitor AWS resources for security incidents. By understanding this shared responsibility, customers can work collaboratively with AWS to ensure a secure cloud environment.
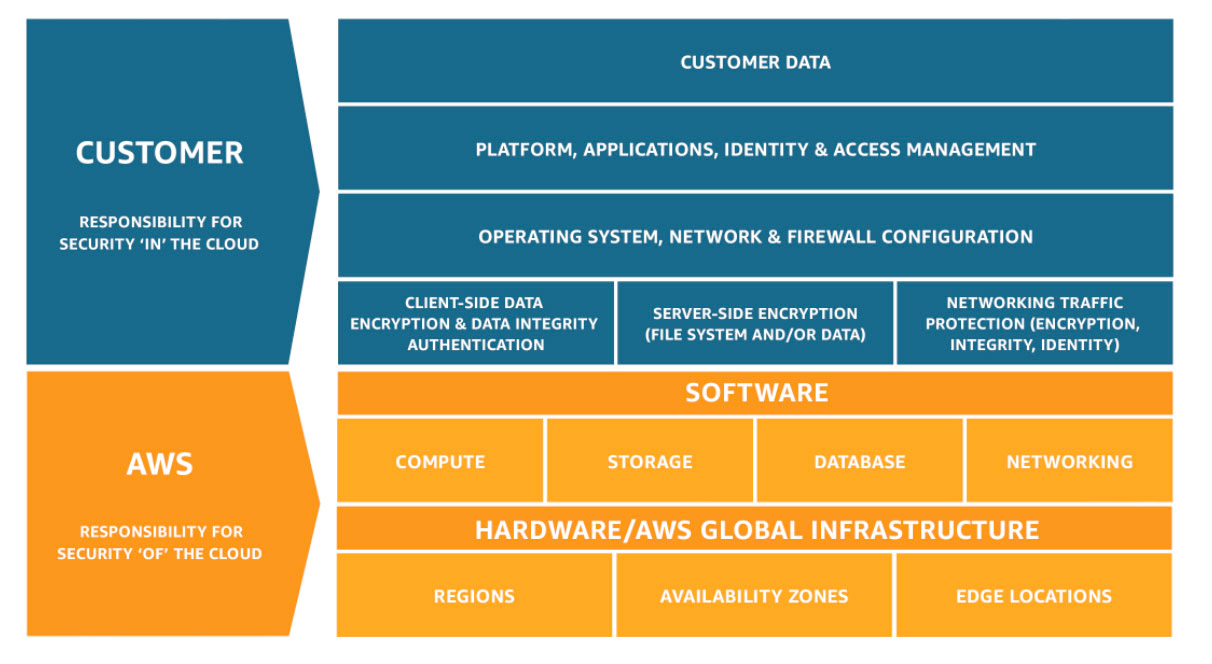
Here
are eight considerations organizations, particularly security engineers,
solutions architects, and IT staff, need to keep in mind when using a cloud
services provider like AWS.
1. Identity and Access Management (IAM)
IAM is a fundamental component of AWS security. Implementing strong access controls and adhering to the principle of least privilege is essential. Create individual IAM user accounts for each user, assigning appropriate permissions based on their roles. Utilize AWS Identity and Access Management (IAM) policies to define fine-grained access controls. Regularly review and audit IAM roles using IAM access analyzers (it's a free tool from AWS) to remove unnecessary privileges and ensure that only authorized users can access AWS resources.
2. Secure Network Architecture
Designing a secure network architecture is vital to protect data in transit and mitigate the risk of unauthorized access. Leverage Amazon Virtual Private Cloud (VPC) to create isolated network environments. Implement network access control lists (ACLs) and security groups to control inbound and outbound traffic at the subnet and instance levels. Utilize AWS Web Application Firewall (WAF) and AWS Shield to protect against common web-based attacks. Implement secure connectivity options such as AWS Direct Connect or Virtual Private Network (VPN) for secure communication between on-premises infrastructure and AWS resources.
3. Data Encryption
Protecting data at rest and in transit is critical for maintaining AWS security. AWS offers multiple encryption options to safeguard sensitive information. Utilize AWS Key Management Service (KMS) to manage encryption keys securely. Encrypt sensitive data using server-side encryption mechanisms provided by AWS services such as Amazon S3, Amazon RDS, or Amazon EBS. Implement SSL/TLS certificates for secure communication with AWS services. Regularly rotate encryption keys and update SSL/TLS certificates to maintain the highest level of security.
4. Monitoring and Logging
Establishing robust monitoring and logging practices enables the detection and response to security incidents in a timely manner. Leverage AWS CloudTrail to monitor API activity and track changes made to AWS resources. Enable AWS Config to assess resource configurations for compliance and security purposes. Utilize Amazon CloudWatch to monitor system performance and set up alarms for security events. Centralize logs using services like Amazon CloudWatch Logs or Amazon Elasticsearch Service for effective analysis and threat detection. Implement automated log analysis and anomaly detection using tools like AWS Security Hub or third-party solutions.
5. Patch Management and Vulnerability Scanning
Regularly applying patches and updates is crucial to address vulnerabilities and protect AWS resources. Keep track of security advisories and patches released by AWS and promptly apply them to your infrastructure. Utilize AWS Systems Manager to automate patch management across multiple instances. Conduct regular vulnerability scanning using tools like AWS Inspector or third-party solutions to identify and remediate potential security weaknesses. Implement secure software development practices, including secure coding and third-party library management, to minimize the risk of vulnerabilities in your applications.
6. Disaster Recovery and Backup
Having a robust disaster recovery (DR) strategy is essential to ensure business continuity and data resilience. Implement AWS services such as Amazon S3 for secure and durable storage of backups. Leverage AWS Database Migration Service (DMS) or AWS Snowball for data migration and offline backups. Utilize AWS CloudFormation or infrastructure-as-code tools like AWS CDK or Terraform to automate the provisioning of resources in DR environments. Regularly test and validate your DR plan to ensure its effectiveness in case of a security incident or disaster.
7. Secure Serverless Architecture
As serverless computing becomes increasingly popular on AWS, it is essential to implement security measures specific to serverless architectures. Apply fine-grained IAM roles and permissions to serverless functions, granting them only the necessary privileges. Utilize AWS Lambda environment variables or AWS Systems Manager Parameter Store to securely store sensitive configuration information. Implement function-level and resource-level access controls to prevent unauthorized access. Regularly scan serverless functions for vulnerabilities and leverage AWS services like AWS Lambda Layers for secure code reuse.
8. Incident Response and Forensics
Preparing for and responding to security incidents is crucial to minimize the impact of potential breaches. Develop an incident response plan outlining roles, responsibilities, and communication channels. Leverage AWS services like AWS CloudFormation and AWS Config to quickly restore a known good state in the event of an incident. Implement AWS CloudTrail and AWS Config rules to detect and respond to security events. Conduct regular tabletop exercises and incident response drills to test the effectiveness of your response plan. Consider leveraging AWS Partner Network (APN) partners specializing in incident response and forensics for additional support.
Sample Code Snippet: Automating AWS Security Group Configuration
Here's an example of a Python script using the Boto3 library to automate AWS Security Group configuration:
Python
import boto3
import sys
# Create an EC2 client
try:
ec2_client = boto3.client('ec2')
except Exception as e:
print("Error in creating EC2 client: ", str(e))
sys.exit(1)
# Define the security group properties
group_name = 'MySecurityGroup'
description = 'Example security group'
vpc_id = 'vpc-12345678'
# Define the ingress rule
# Be sure to replace 'your-ip/32' with the actual IP address you want to allow.
ingress_rule = {
'IpProtocol': 'tcp',
'FromPort': 443,
'ToPort': 443,
'IpRanges': [{'CidrIp': 'your-ip/32'}]
}
# Create the security group
try:
response = ec2_client.create_security_group(
GroupName=group_name,
Description=description,
VpcId=vpc_id
)
except Exception as e:
print("Error in creating security group: ", str(e))
sys.exit(1)
# Add the ingress rule to the security group
try:
ec2_client.authorize_security_group_ingress(
GroupId=response['GroupId'],
IpPermissions=[ingress_rule]
)
except Exception as e:
print("Error in adding ingress rule: ", str(e))
sys.exit(1)
print("Security group created with ID:", response['GroupId'])
)
# Add the ingress rule to the security group
ec2_client.authorize_security_group_ingress(
GroupId=response['GroupId'],
IpPermissions=[ingress_rule]
)
print("Securit group created with ID:", response['GroupId'])
Establishing a secure cloud environment on AWS requires a comprehensive approach that encompasses various aspects of security. By considering key factors such as IAM, secure network architecture, data encryption, monitoring and logging, patch management, and disaster recovery, organizations can enhance their AWS security posture and protect their valuable assets in the cloud.
It is important to continuously stay updated with the latest AWS security best practices, leverage AWS security services, and regularly review and improve security measures to effectively mitigate risks and safeguard your AWS resources. Remember, AWS security is a shared responsibility between AWS and customers, and by implementing the right security measures, organizations can confidently harness the power of AWS while maintaining a strong security posture.
We Provide consulting, implementation, and management services on DevOps, DevSecOps, DataOps, Cloud, Automated Ops, Microservices, Infrastructure, and Security
Services offered by us: https://www.zippyops.com/services
Our Products: https://www.zippyops.com/products
Our Solutions: https://www.zippyops.com/solutions
For Demo, videos check out YouTube Playlist: https://www.youtube.com/watch?v=4FYvPooN_Tg&list=PLCJ3JpanNyCfXlHahZhYgJH9-rV6ouPro
If this seems interesting, please email us at [email protected] for a call.
Relevant Blogs:
Recent Comments
No comments
Leave a Comment
We will be happy to hear what you think about this post