Examining the Strengths and Applications of Modern Security Models

It is crucial to know the different security models, their features, and their suitability for specific situations.
In the world of computing, security plays a crucial role in safeguarding resources. Over the past decade, various security models have been created to ensure the confidentiality, integrity, and availability of information. They present methods that organizations can adopt to establish formal policies for information security. These policies aim to provide a structured approach for deploying security measures and practices to safeguard sensitive information and prevent security breaches. Having knowledge about different security models, their features, and their suitability for specific situations is crucial. It enables one to make informed decisions on selecting the appropriate security model that can effectively address security concerns and protect computational resources.
Access Control Models
One of the most utilized models, Access Control, is designed to assist in the creation of policies related to system/user-level access for diverse resources such as files, databases, and networks. The rule of thumb is to only provide access to the entity that they need to perform their duties. This model encompasses three main types of controls; Discretionary Access Control (DAC), Mandatory Access Control (MAC), and Role-based Access Control (RBAC). With DAC, a resource owner has the capability to decide 'who can access what?'. For example, the owner of a file decides who they want to grant access to and in what capacity (editing or viewing rights). Due to its versatility and ease of use, the DAC model is commonly adopted by smaller organizations.
On the other hand, industries like defense, administration, etc., prefer very restrictive control policies like MAC. Access restrictions in the MAC model can be enforced based on the security labels assigned to resources. These labels determine the level of security clearance required to access the resource. They also enable a structured approach to implementing security measures and preventing unauthorized access to sensitive data. However, most organizations need a middle ground, a control that is not too restrictive but also not very liberal. In such scenarios, RBAC is the most suitable. It grants access based on the assigned user's role in the organization. This enables organizations to easily modify access permissions when there is a change in the role without the need for modifying access rights for each individual user.
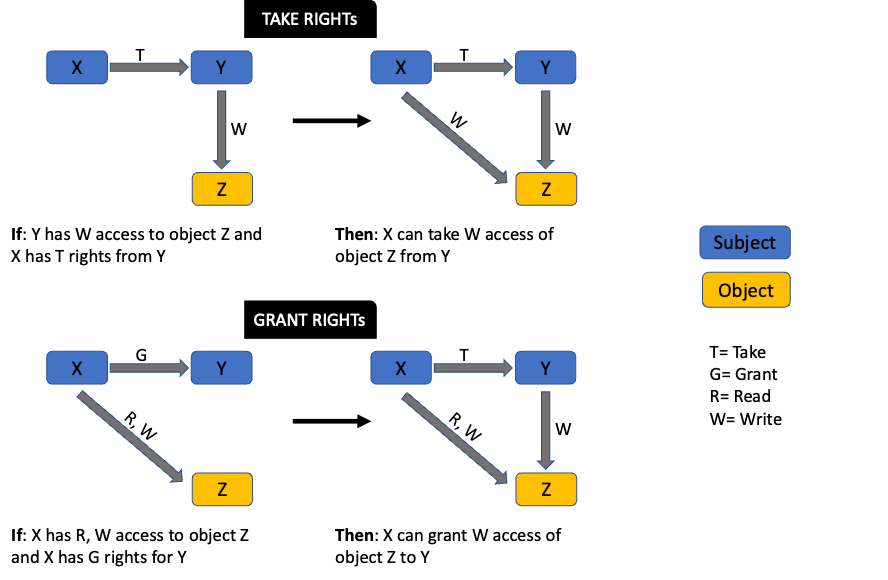
Take-Grant Model
This model relies on the concept that individuals can grant or take permissions to and from other individuals or entities. The effectiveness of this model can be clearly evaluated by a directed graph representation. There are two broad rules under this model. With the 'take rule,' a subject can take rights from another subject, while the 'grant rule' allows a subject to grant its access to another subject.
For example, an employee in the marketing department has access to marketing assets, while an employee in the IT department has access to sensitive technical information. If the marketing team member requires access to a technical document, they will need to request someone with grant rights to the resource. In this case, that might be an IT supervisor.
Below is a directed graph for the Take-Grant model. Notice how rights can be passed from one subject to another or from a subject to an object.
Biba Model
This model has a design that is very similar to Bell-LaPadula, with the main difference being its focus on data integrity. It is also based on the information flowing within a multi-level security system with levels assigned to resources. The two main components of this model include the Simple Integrity Property (SIP) and the * (star) Integrity Property. Within SIP, the data at a given level cannot be read by a user at a higher security level, a.k.a. 'no read down.' E.g., a senior engineer cannot read code changes made by the junior engineer until they are committed. Under the star integrity property, data at a given level cannot be modified by a user at the lower level, a.k.a. 'no write up.' Institutions like finance and healthcare usually adopt this model to protect patient records and other sensitive information.
Clark-Wilson Model:
Data integrity is the primary focus; this model allows limited modification through a controlled interface/access portal. For users, there is a separation of duties, and their resource access is limited. This model has three main components: the Constrained Data Item (CDI), Integrity Verification Procedure (IVP), and Transformation Procedure (TP). CDI has access controls enforced that ensure authorized access. IVPs are used to check data integrity. After the integrity of the data-in-use is established, Transformation Procedures govern modifications taking place. This model is widely used in e-commerce and finance industries where data integrity and security are vital.
Based on the concept of separating security levels and information flow, this model focuses on confidentiality. Its two main components are High-Level Security and Low-Level Security. Actions performed on higher-level security should not impact or even be noticeable for users at lower-level security. This prevents information leakage and provides protection against covert programs like trojan horses and backdoors. It is widely used in the government or military where secure information flow is critical.
Trusted Computing Base (TCB)
As the name suggests, this model ensures that all computing resources used within an organization are trusted and free from security vulnerabilities. Its four main components are Security Policy, Security Kernel, Reference Monitor, and Security Perimeter. The overall secure functioning of the system is defined under the security policy. Resource access is mediated at the security kernel. The reference monitor validates authorization for each resource before granting access. Finally, the security perimeter blocks or restricts access from the outside world to the company resources. Most of the top technology organizations use TCB to ensure that systems are designed securely.
Brewer and Nash Model
Widely used in legal and consulting, this model prevents conflict of interest when employees have access to critical data pertaining to different clients. It is also known as the Chinese Wall model because it is based on a concept of a wall that partitions data to prevent unauthorized access. Creating logical and/or physical segregation of data warrants that one client's data cannot be accessed by employees working with another client.
Graham-Denning Model
This model is based on the secure creation of a subject and object. It defines who can access/change what data. Mainly centered on data integrity and access control, it establishes the fact that only authorized subjects can access the data object. It is used widely in banking and e-commerce sites where customer account information and their transactions/purchases are important to protect. It has eight primary rules containing the creation/deletion of subjects and objects securely while ensuring secure read, writing, delete, and grant access rights.
Harrison-Ruzzo-Ullman Model
An extension of Graham-Denning, this model is used to ensure backend system security like OS (Operating systems) and databases. It defines a set of procedures that provide access rights to the subject/user. This can be represented using a matrix where subjects and objects are organized in rows and columns respectively. An additional control has been introduced to enable modification rights for the matrix, while integrity rules have been implemented to ensure that users cannot create new subjects or objects that violate system-level validation requirements. One clear application of this model is in operating systems, where access to system resources is determined by authorization levels. Therefore, users can only utilize the resources they have been authorized to access.
Across these models, there are various security controls available that will ensure secure and accurate systems. Here are some factors that can help an organization pick the controls that fit its needs and system capabilities:
- Common Criteria (CC): This is a set of criteria used to evaluate and validate the security features of a system. It involves a rating-based approach and is designed to provide a subjective evaluation of a product. CC comprises two key elements: protection profiles, which specify the security requirements that a product must meet, and security targets, which evaluate the measures taken by an organization to safeguard its product.
- Authorization To Operate (ATO): As part of a risk-based approach, obtaining official approval is required prior to using any resource or product. This is known as the 'Authorization to Operate.' There are four key decisions that an authorizing official can take: authorization to operate, common control authorization, authorization to use, and denial of authorization.
- Interfaces: An application can incorporate a constrained or restricted interface to limit users' access or visibility according to their authorized privileges. If a user has full privileges, they will be able to access all the capabilities within an application. On the flip side, if they have restricted privileges, they will have access to limited parts of the application. For example, an end user should never be able to see the admin console. Different methods can be used to introduce constraints based on the criticality, exposure, and the identified attack surface for the application/interface. For example, Clark Wilson model can be deployed if the actions of both authorized and unauthorized users need to be restricted.
Other system capabilities and requirements that might be good to consider include encryption level, HSM (Hardware security module), fault tolerance, virtual machines requirement, and kernel-level protection.
Once the requirements and capabilities are identified, the next step is to decide about the security model. Here are some sample 'requirement: model' mappings:
- Data confidentiality of sensitive data: Bell-LaPadula Model
- Prevent unauthorized data modification: Biba Model
- Data integrity in the business world: Clark-Wilson Model
- Prevent Conflict of interest: Brewer and Nash Model
- System security with required cryptographic protocols: Goguen-Meseguer Model
- Access control in Finance sector: Graham-Denning Model
- Security of OS and DBMS: Harrison-Ruzzo-Ullman Model
Each model has its strengths and limitations. Hence, it is important that security controls are selected based on the organization's needs and system requirements. Each industry, such as government, military, healthcare, and finance, requires specific security models that are well-matched to their unique needs. The choice of model will also depend on the data criticality and level of access that can be granted. The goal is to ensure that the organization's computing resources and systems are secure enough to prevent unauthorized access or modification. The efficiency of these models should be tested on a periodic basis through security assessments and internal audits, hence keeping them safe from cyber threats.
We Provide consulting, implementation, and management services on DevOps, DevSecOps, Cloud, Automated Ops, Microservices, Infrastructure, and Security
Services offered by us: https://www.zippyops.com/services
Our Products: https://www.zippyops.com/products
Our Solutions: https://www.zippyops.com/solutions
For Demo, videos check out YouTube Playlist: https://www.youtube.com/watch?v=4FYvPooN_Tg&list=PLCJ3JpanNyCfXlHahZhYgJH9-rV6ouPro
If this seems interesting, please email us at [email protected] for a call.
Relevant Blogs:
How To Use Artificial Intelligence to Ensure Better Security
Don’t Rely Solely on Privileged Access Management (PAM) To Secure Your Accounts
DevSecOps: The Future of Secure Software Development
Recent Comments
No comments
Leave a Comment
We will be happy to hear what you think about this post