HIPAA Compliance Testing In Software: Building Healthcare Software With Confidence
This article covers HIPAA compliance testing in Health care solutions.
HIPAA has governed the healthcare software market for almost three decades. But, as ubiquitous as it is, not every healthcare organization is either willing to make sure their application is compliant with HIPAA or has the skills and resources to develop HIPAA-compliant software. As a result, over 231 million US citizens have become victims of healthcare data breaches over the years.
In many cases, companies lose money in settlements due to failing to comply with HIPAA regulations, and in 100% of the cases, companies end up sacrificing their reputation among patients and partners. One of the most effective ways to ensure compliance with HIPAA requirements and subsequent safety of patient data is through HIPAA compliance software testing, and that’s what we’ll talk about today.
What Is HIPAA and What Are the Key HIPAA Requirements?
HIPAA, which stands for Health Insurance Portability and Accountability Act, is a legal document outlining the ways healthcare providers need to manage the data of their patients. HIPAA was enacted for multiple reasons, but most importantly, to keep patient health information secure and to ensure complete access control only for authorized parties. Moreover, HIPAA became instrumental in switching from paper to digital when managing and transferring patient records.
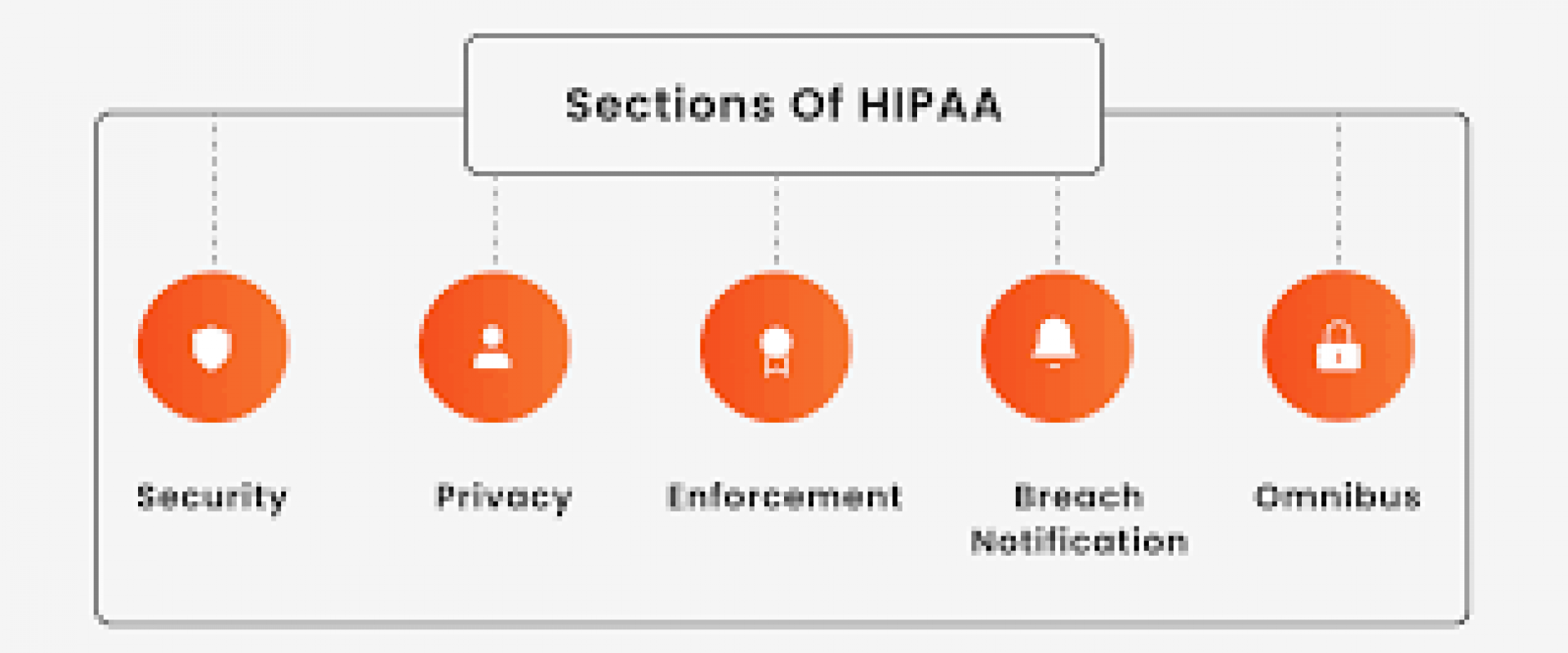
HIPAA is divided into five sections, or titles, each having to do with different aspects of sensitive patient data protection and management. The titles include the following segments of software in the healthcare industry.
1. Security
Under the security section of HIPAA requirements, there are three safeguard types: technical, physical, and administrative.
HIPAA technical safeguards include the following points:
- There must be a strategy for safely releasing patient data in case of an emergency.
- Data must be encrypted at the point where it leaves the internal firewall.
- All users accessing patient information must be regularly logged out on their devices.
- There should be a technical ability to know when the data has been tampered with by a third party.
Here are some physical safeguards outlined by HIPAA:
- There must be a regularly updated list of locations where sensitive data can be accessed.
- Each hardware device dealing with healthcare data must be accounted for.
- If an employee can access the data from their mobile device, the data must be wiped after the employee leaves the organization.
- There should be a set of clearly outlined policies for users with access to data.
Finally, these are the administrative safeguards to consider:
- Risk assessment and risk management policies should be in place.
- If any third parties have access to the data, a business associate agreement must be signed.
- There needs to be a security and privacy officer at the organization.
- There must be a contingency plan detailing the company’s security efforts.
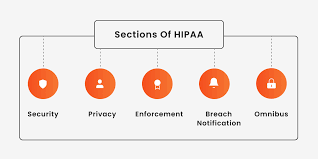
2. Privacy
- You must obtain the customer’s consent before using their data for marketing or research purposes.
- There needs to be an NPP (Notice of Privacy Policy) and an additional policy in case someone does not comply with the NPP.
- Your privacy principles need to be outlined and open to the public.
- If a customer requests a copy of their record, you must be able to provide it within 30 days.
3. Enforcement
- There must be access and authentication protocols in place.
- Encryption must be used to protect PHI (Protected Health Information).
- You must ensure that any third-party tech partner helping develop or test your software is also HIPAA-compliant.
- Security risk assessments must be performed regularly.
4. Breach notification
- The responsible parties should be able to identify a breach quickly.
- There must be a clearly defined procedure to deal with a data breach.
- Users, partners, and authorities must be notified in case of a breach.
- If more than 5,000 patients are affected by the breach, the media should also be notified.
5. Omnibus
- A HIPAA Privacy and Security Awareness Training Program should be made available to all employees.
- You must provide an electronic copy of the patient’s record should they request it.
- The breach notification compliance plan should be regularly updated.
- Your ePHI must always comply with the newly introduced standards.
Why Does Healthcare Software Need To Be HIPAA-Compliant?
To prevent data loss, the US Department of Health has introduced fines for companies whose products do not meet HIPAA compliance. The fines can range from $100-$50,000 for organizations that did not know about the data breach to up to $1.5 million when the company willingly did not comply with HIPAA requirements. There were known cases when the company reached a settlement with the victims amounting to $16 million. However, the chance of getting fined is certainly not the only reason to align your software with HIPAA guidelines.
The main reason to prepare your software for HIPAA compliance is that a software product meant to help people with the most sensitive subjects should have their complete trust. Gaining trust is never easy, but regaining it after a security breach is harder than anyone can imagine. This is the part of HIPAA that is not outlined in the official documentation but has an immediate impact on the present and future of your application.
“Among other things, HIPAA compliance is there to protect the lives of the patients and data sensitivity, and while this, in turn, protects the company’s reputation, in the event that there is a failure or a breach, then the company can be fined large sums of money, which is another strong reason for healthcare companies wanting to ensure that they stay within the compliance rules.”
Bruce Mason, Head of Delivery, TestFort
Who Is Required To Be HIPAA-Compliant?
Historically, health and human services in the US have a long and often complicated supply chain. This is why the HIPAA guidelines apply not only to the immediate healthcare providers, including hospitals and individual doctors but also to a variety of other individuals working in the healthcare field:
- Health insurance companies
- Health plan providers
- Software service providers (infrastructure and cloud storage providers)
- Medical billing companies
- Transcriptionists
Who Should Do Testing To Ensure HIPAA Compliance?
Defining the testing in the HIPAA segment of QA is one thing, but an equally important question is: “Is testing healthcare software difficult, and if so, who should do it?” To answer the first part of the question, HIPAA software testing is usually more complex than other QA activities because there are so many regulations to take into account and so many different but equally important, detailed test cases to prepare. Therefore, the best HIPAA software testing engineers are the ones who have not only deployed healthcare apps before but are also familiar with the specifics of testing for HIPAA compliance. This is why most companies prefer to work with QA teams who are HIPAA-certified.
“Our clients normally insist on all people being HIPAA-certified within the team. This is a small set of learning requirements people have to go through and complete a small test at the end. So the question is: why do this? Well, it focuses people’s mindset on understanding what is needed for HIPAA within the project team and ensures everyone has the same approach and understanding of what is needed for the Product to be compliant in the Industry.”
Bruce Mason, Head of Delivery, TestFort
The exact composition of the team will depend on several factors, including the size of the application, the end goal of testing, the specifics and amount of test data used, and so on. Typically, the QA team for testing a healthcare app for HIPAA compliance will include the following members:
- QA engineers
- HIPAA compliance consultant
- Test manager
- Infrastructure Engineer
- Security test engineer
- Automation QA
When To Do HIPAA Compliance Testing?
Given the sensitive nature of patient information protected by HIPAA and the many examples of companies suffering financial and reputation losses due to failure to comply with the regulations, the importance of HIPAA compliance software testing is not to be argued with. However, there are three situations where HIPAA testing proves to be particularly integral:
1. When you are about to release a new healthcare application into the market.
2. When there are significant changes to the existing application, i.e., new functionality.
3. When HIPAA regulations have recently been updated.
“At least every year, every healthcare company is audited to ensure that they are still compliant with the regulations that HIPAA defines. If there are any exceptions, these are advised to the company for correction. Obviously, these exceptions come in different categories, some of which are minor breaches and do not affect Patient Care. Others are more serious and need to be corrected quickly. Of course, larger exceptions can force a company to be shut down or be fined by the organization.”
Bruce Mason, Head of Delivery, TestFort
How to Comply With HIPAA With the Help of Software Testing
In an ideal scenario, healthcare applications must follow HIPAA regulations already at the software development stage. However, HIPAA compliance should become a continuous work in progress: as the software changes due to updates or enhancements, and as HIPAA requirements get more sophisticated, HIPAA compliance testing in software applications dealing with healthcare becomes a standard part of developing and testing software. But how exactly do you develop a HIPAA compliance testing plan, and what should you include in one?
It’s worth noting that there cannot be a universal testing and QA strategy for HIPAA compliance in software testing because the products themselves can be very different, and there can be different amounts of HIPAA testing done previously. This is why it’s vital to check the software documentation first to find out what has already been done in the HIPAA compliance software testing areas. Here is what else your healthcare software testing strategy needs to include if you want to ensure that the product is compliant with HIPAA.
1. Functional and Non-Functional Testing
When you are getting ready to release a new software product or an updated version of an existing product, HIPAA compliance is not the only area that needs your attention. The compliance of the application with both non-functional and functional requirements has an immediate impact on the way the audience interacts with the product and whether the users are likely to turn into loyal customers. This, in turn, influences both the company’s reputation in the market and its revenue. So whether you do functional testing and non-functional testing simultaneously with HIPAA-related testing activities or have them precede HIPAA compliance testing, this step is not to be missed.
This stage is strongly linked to sanity testing, where the team covers major HIPAA compliance software roles and functionality to make sure they’re all there and ready for further testing.
2. Roles Matrix
One of the principles of a HIPAA-compliant application is role-based access, where different categories of authorized users have different access levels. To make it happen and to test it with maximum efficiency, there needs to be a role matrix. For each role, there should be a risk analysis, which is then displayed in the matrix using color coding. Typically, red means high-risk operations, yellow indicates medium risk, and green means low risk. The healthcare software development team will usually look at a few factors to determine the risk level, including the need for information disclosure, the likelihood of errors, and how much the customers are going to be affected in the negative scenario.
3. Security Testing and Penetration Testing
By its nature, security testing is at the heart of software compliance and is one of the major HIPAA compliance software testing components. Security testing is meant to verify that the product has all the protection from unauthorized use and data breaches it needs. It’s also a good idea to invest in penetration testing — as an advanced subsection of security testing, penetration testing helps find even the smallest flaws within the software. The technique where QA engineers pose as hackers also helps identify security bottlenecks and prevent breaches in the future.
4. Test Cases
A test case is a valuable piece of test data that tells the team exactly what needs to be tested. Regarding test cases, HIPAA software testing must cover five key areas:
- Information disclosure — primarily, this includes role-based access to different types of information and patient allocation to a specific provider for a specific amount of time.
- User authentication — an area that deals with positive login scenarios (including username and password, fingerprint, or ID cards), as well as negative scenarios (login timeout, password change, repeated failed attempts)
- Audit trails — an operation meant to make sure that audit trail entries are the same or close to the expected entries. Moreover, the audit trails need to be encrypted and impossible to remove for specific access levels.
- Data transfer — in HIPAA compliance, not only audit trails and databases need to be encrypted, but also PHI when it’s transferred between mobile devices, sent to a different location, or moved to an offline storage facility.
- Correct data use information — every page within the application needs to include a link to a source where correct data use is explained, in addition to describing the operations linked to ePHI.
5. Testing Automation
While some aspects of HIPAA compliance testing can only be done manually, automated testing tools can significantly enhance the testing project and help obtain more reliable results. Automation testing can be particularly useful in security and penetration testing when the team needs to use a variety of scenarios to make sure the testing process is complete. It can also come in handy with regression testing, saving the team time and resources on repeated tasks.
Best Practices To Achieve and Maintain HIPAA Compliance
We’ve already talked about the areas you need to check when ensuring the compliance of your application with HIPAA rules. However, some additional guidelines will help you make sure your app is fully ready to be scrutinized even by the most demanding HIPAA compliance officer.
- Appoint a responsible individual. You may have a large testing and QA team, but there needs to be one person (i.e., a security officer) who will oversee the entire process and be aware of all the changes and the subsequent steps the team needs to take to ensure compliance.
- Keep track of data movements. Whenever patients or providers enter healthcare data, or it’s transferred to another physical or cloud storage location, or any other significant or minor changes occur, the changes need to be recorded and the data management strategy needs to be adjusted.
“Data transfers between systems can become very complicated, and make up a large part of systems in the Healthcare Domain. As such, they have standardized this using HL7 or FHIR as approaches, and these are the most common languages that are used (especially in the US).”
Bruce Mason, Head of Delivery, TestFort
- Train and update your employees. In addition to the security officer or a person in a similar management position, the day-to-day tasks of ensuring compliance with HIPAA will be done by your employees. This is why they need to have a complete idea about HIPAA and what they can do to ensure it.
- Make sure your business partners are compliant too. These days, healthcare software products rarely exist in isolation, as software development companies have come to rely on third-party partners for infrastructure, additional services, and so on. It’s vital to ensure that the partners are also HIPAA-certified.
- Have a breach reaction policy. Security breaches seem almost inevitable, but how you react to them will greatly impact your business reputation. It’s also one thing to react properly to a breach, but even being aware of a recent breach is not always easy. This is why your breach-related policies need to be robust and regularly reviewed.
Factors Influencing the Cost of HIPAA Compliance Testing
Before we talk about the cost of testing your software for HIPAA compliance, we need to answer one question: Who is going to test the software application and see if it complies with HIPAA rules? There are several directions your project can go in terms of the team. First, you can entrust the work to your in-house QA department, provided that you have one and that the members of your testing team are familiar with the ins and outs of HIPAA compliance.
Another option is to create a HIPAA testing department from scratch, hiring only the most knowledgeable engineers with relevant healthcare experience. The downside of this method is that it takes a lot of time and money to establish a brand-new department, so it may be a while before you start getting results. Plus, hiring an entirely new team doesn’t always make sense when you only need to test one application and may not need a long-term commitment.
This is why many companies that want to be HIPAA-compliant now prefer to outsource their testing needs to an outside vendor. This method has multiple benefits for a project:
- Cost-effectiveness — you don’t need to take care of hiring, office space, equipment, or onboarding.
- Niche expertise — you get to choose specialists who are experts in exactly the right field.
- Flexibility — you can hire a team for a limited time and scale the cooperation up and down as needed.
Of course, before you make any commitment, you need to make sure that the QA engineers are equipped to tackle the challenges specific to your project. At the very least, you need to ensure they have experience with healthcare applications and HIPAA regulations. It’s also a good idea to work only with engineers who are HIPAA-certified: this is the main sign that they know their way around HIPAA compliance.
Now let’s move on to the question of costs. While keeping your budget lean is not the only reason to consider outsourcing, it’s still one of the main reasons why companies do it at all. There can be a significant difference in the prices: an in-house Junior Software QA in the US can cost you around $60 per hour, while an engineer with similar qualifications in Eastern Europe costs only $20-30 per hour. The price difference can be even more stark for more experienced engineers with niche expertise. In addition to that, the following factors typically influence the cost of a HIPAA compliance testing project:
- The nature and complexity of the application
- The current state of HIPAA compliance
- The relevant technical testing safeguards
- The required types of testing
- The number and complexity of the test cases
- The need for testing automation and its scale
- The use of paid testing tools (including security and penetration)
Final Thoughts
If you work in the healthcare software domain, making your product compliant with HIPAA is not just an option to consider — it’s what your business requires to take its rightful place on the market and ensure a decent reputation among customers, business partners, and authorities. It’s important to continuously think about HIPAA requirements already at the development stage and regularly engage in HIPAA compliance test efforts to protect the application from preventable security issues and subsequent revenue and reputation losses.
We Provide consulting, implementation, and management services on DevOps, DevSecOps, DataOps, Cloud, Automated Ops, Microservices, Infrastructure, and Security
Services offered by us: https://www.zippyops.com/services
Our Products: https://www.zippyops.com/products
Our Solutions: https://www.zippyops.com/solutions
For Demo, videos check out YouTube Playlist: https://www.youtube.com/watch?v=4FYvPooN_Tg&list=PLCJ3JpanNyCfXlHahZhYgJH9-rV6ouPro
If this seems interesting, please email us at [email protected] for a call.
Relevant Blogs:
Searchable Pod Logs on Kubernetes in Minutes
O11y Guide: Keeping Your Cloud-Native Observability Options Open
Recent Comments
No comments
Leave a Comment
We will be happy to hear what you think about this post