How To Adopt Shift Left Security on the Cloud
This article delves into the essential strategies and practices that enable organizations to adopt Shift Left Security seamlessly in their cloud environments.
In an era where cloud computing reigns supreme, the concept of security has undergone a profound transformation. As businesses rapidly migrate their operations and data to the cloud, the need to secure this digital frontier becomes increasingly paramount. Enter "Shift Left Security," a paradigm shift in cybersecurity that places the emphasis on prevention and early detection rather than reaction. In this blog, we'll delve into the essential strategies and practices that enable organizations to adopt Shift Left Security seamlessly in their cloud environments.
Imagine a world where security vulnerabilities are identified and remedied at the earliest stages of software development, long before they have a chance to evolve into costly breaches. Shift Left Security makes this vision a reality by pushing security considerations to the forefront of the cloud development process. It's a proactive approach that ensures that security is not an afterthought but an integral part of the cloud pipeline components and ecosystem from the very beginning.
Join us on this journey as we explore the principles, tools, and best practices that empower you to fortify your cloud-based infrastructure and applications and dynamic pipeline safeguarding your digital assets. Here, we’ll guide you in adopting Shift Left Security and keeping your cloud environment resilient in the face of ever-evolving threats.
What Is Shift Left in CI/CD?
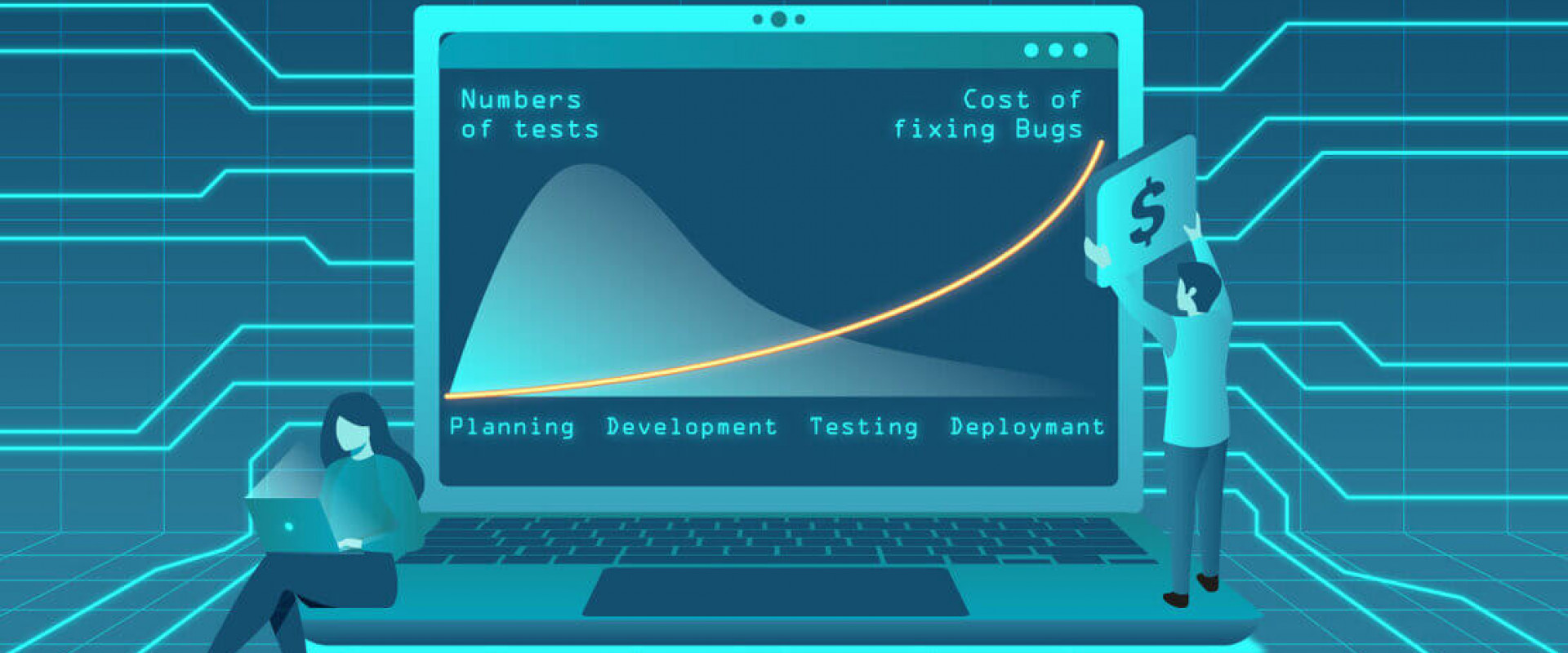
Shift Left in the context of Continuous Integration and Continuous Deployment (CI/CD) refers to the practice of moving tasks and processes that traditionally occur later in the software development lifecycle (SDLC) to earlier stages. The goal of shifting left is to identify and address issues as early as possible in the development process. This helps in improving the quality of the software and accelerating the delivery of new features and updates.
In a traditional SDLC, testing, CI/CD security checks, and other quality assurance activities happen closer to the end of the development process, after the code has been written and integrated. This can lead to delayed detection of issues, longer feedback loops, and higher costs to fix problems that are identified late in the process.
By shifting these activities to the left—meaning they are conducted earlier in the development process—you can achieve several benefits:
- Early Issue Detection: By performing testing, security scanning, and code analysis earlier, you can identify and address issues sooner. This reduces the likelihood of defects and vulnerabilities making their way into the final product.
- Faster Feedback Loops: Developers receive feedback more quickly, enabling them to make necessary adjustments and improvements without causing delays further down the line.
- Cost Efficiency: Fixing issues earlier in the SDLC tends to be less expensive than fixing them after they've reached production. This can save time, effort, and resources.
- Improved Collaboration: Shifting left encourages better collaboration between development, testing, and operations teams, as everyone is involved in identifying and addressing issues from the outset.
- Faster Time to Market: With fewer defects and quicker feedback cycles, software can be deployed more rapidly, allowing faster delivery of features and updates.
- Enhanced Security: By incorporating security assessments and checks earlier in the development process, vulnerabilities can be identified and mitigated before they become significant risks.
To implement a shift left approach, cloud pipeline components are designed to include automated testing, code analysis, security scanning, and other quality checks as part of the development process, starting from the moment code is committed. This way, any issues are caught early, allowing developers to make adjustments and corrections promptly.
Overall, the shift left philosophy aims to create a more efficient and effective development process by emphasizing proactive quality assurance practices and collaboration among cross-functional teams.
Ways To Adopt Shift Left Security on the Cloud
Adopting Shift Left Security in the cloud involves integrating security practices and considerations early in the software development lifecycle (SDLC) and throughout your cloud infrastructure deployment process. This proactive approach helps identify and mitigate security vulnerabilities and threats at an early stage, reducing the chances of security incidents and the associated costs and risks. Here's a step-by-step guide on how to adopt Shift Left Security in the cloud and integrate security in DevOps:
· Define Security Policies and Standards
o Establish security policies, standards, and guidelines for your cloud environment. These should align with industry best practices and regulatory requirements.
· Integrate Security in DevOps
o Embed security into your DevOps pipeline by automating security testing and compliance checks at every stage of development and deployment.
o Use infrastructure as code (IaC) to define and provision your cloud resources, ensuring that security configurations are codified and checked before deployment.
· Implement Continuous Integration/Continuous Deployment (CI/CD) Security
o Integrate security scans into your dynamic pipeline to automatically identify vulnerabilities and misconfigurations in your code and infrastructure.
o Use tools like Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), and Dependency Scanning to identify and remediate security issues early.
· Leverage Cloud-Native Security Tools
o Cloud service providers (e.g., AWS, Azure, Google Cloud) offer native security tools and services that can help you monitor, detect, and respond to threats in your cloud environment.
o Use these tools for services like identity and access management (IAM), network security, and threat detection.
· Automate Security Compliance
o Use tools and scripts to enforce security compliance policies for your cloud pipeline and resources. For example, you can use AWS Config Rules and GitLab CI/CD AWS rules to monitor compliance with security standards.
o Automate the remediation of non-compliant resources whenever possible.
· Implement Least Privilege Access
o Follow the principle of least privilege for user and application access to cloud resources. Limit permissions to only what is necessary for each role or service.
o Use IAM roles and policies to control access to cloud resources.
· Monitor and Detect Threats
o Set up continuous monitoring and logging for your cloud infrastructure. This way, you can easily integrate security in DevOps.
o Implement a Security Information and Event Management (SIEM) system to centralize and analyze security logs and events.
o Use cloud-native threat detection tools to identify and respond to security incidents.
· Incident Response Plan
o Develop an incident response plan specific to your cloud environment. Ensure your team knows how to respond to security incidents effectively.
· Regularly Update and Review
o Periodically review and update your security policies, controls, and tools to adapt to evolving threats and best practices. The GitLab CI/CD AWS review also helps the security team in reviewing cloud security.
· Continuous Improvement
o Encourage a culture of continuous improvement by conducting post-incident reviews, security retrospectives, and sharing lessons learned.
Shift Left Security is an ongoing process that requires commitment and collaboration across teams. By integrating security early in your cloud development and deployment processes, you can better protect your cloud-based applications and data.
In the world of 'Shift Left Security,' we've learned the importance of starting strong and early. Just as we aim to shift security left in our development processes, let's also remember to 'shift left' in our writing.
Final Wrap Up
Shift Left testing supports microservices by promoting early testing, fostering collaboration, and improving code quality. The approach facilitates the fast-paced, iterative development and deployment cycles that Microservices architecture advocates. It helps mitigate risks, reduce defects, and ensures that each Microservice operates as expected within the larger application ecosystem. By using the Shift Left philosophy, developers can ensure that their microservices are reliable, scalable, and efficient.
We Provide consulting, implementation, and management services on DevOps, DevSecOps, DataOps, Cloud, Automated Ops, Microservices, Infrastructure, and Security
Services offered by us: https://www.zippyops.com/services
Our Products: https://www.zippyops.com/products
Our Solutions: https://www.zippyops.com/solutions
For Demo, videos check out YouTube Playlist: https://www.youtube.com/watch?v=4FYvPooN_Tg&list=PLCJ3JpanNyCfXlHahZhYgJH9-rV6ouPro
If this seems interesting, please email us at [email protected] for a call.
Relevant Blogs:
Hyper-V and Quantum Computing: Exploring the Synergy of Future Technologies
Dockerizing ML Models: A Deployment Guide
Introduction To Azure Analytics Architecture Advisor
AWS Resources To Help You Get Started in the Cloud Journey
Recent Comments
No comments
Leave a Comment
We will be happy to hear what you think about this post