Role-Based Multi-Factor Authentication
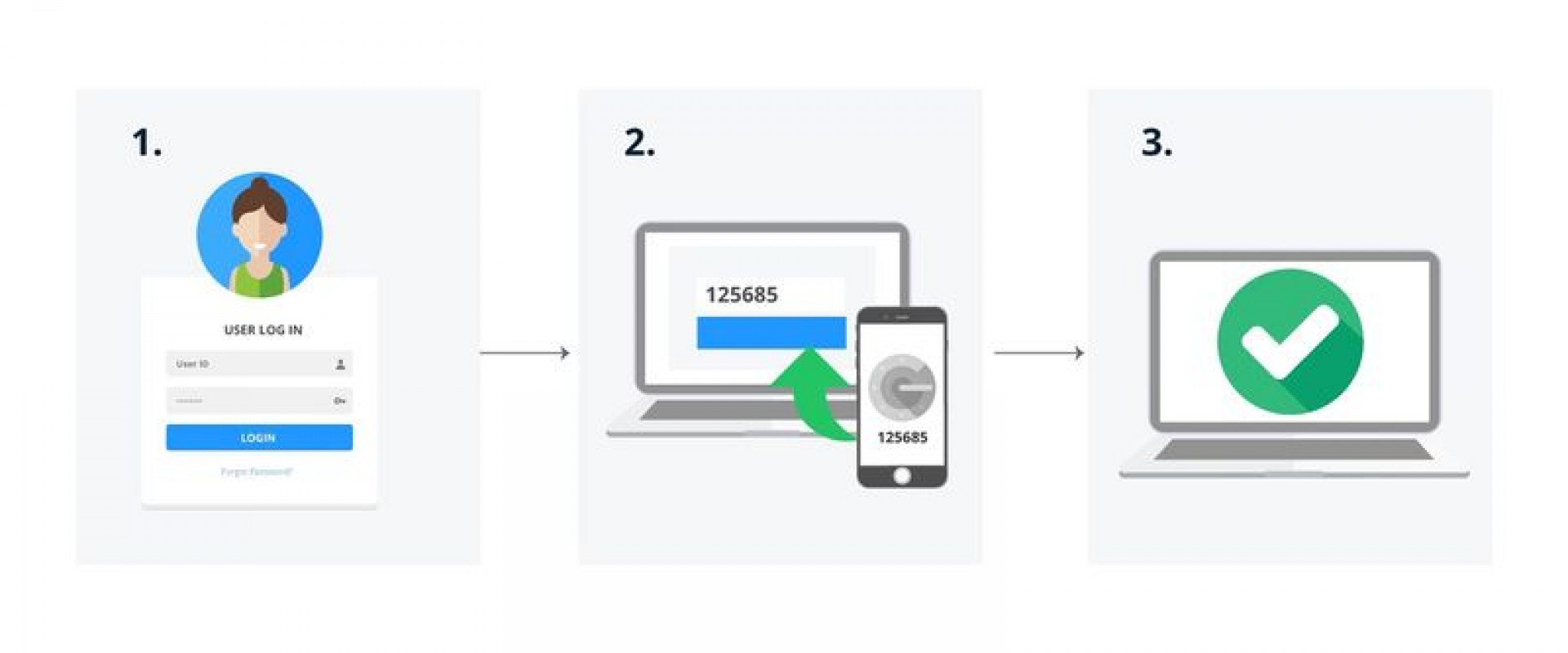
Multi-factor authentication is being adopted by more and more organizations these days because putting it in place greatly increases security.
Multi-factor authentication (MFA) is a method of computer access control in which a user is granted access only after successfully presenting several separate pieces of evidence to an authentication mechanism — typically at least two of the following categories: knowledge (something they know), possession (something they have), and inherence (something they are).
MFA is being adopted by more and more organizations these days because putting it in place greatly increases security. The user also feels more secure. So, why use role-based multi-factor authentication (MFA)? Modern organizations are typically subject to a wide range of regulatory and contractual legal obligations for the security of the data they create and use.
Organizations must be able to demonstrate the steps they have taken to ensure the security and confidentiality of their client's data. They are also bound by law to take such steps. Well-implemented role-based multi-factor authentication provides a high degree of granularity in controlling who has access to what information, and under what conditions access may be obtained, and it is found that the use of MFA can greatly assist in ensuring compliance with the Act.
Such technology not only provides a greater level of protection against data security breaches and ensures the confidentiality and integrity of data critical to the business, but also assists organizations in demonstrating adherence to data protection obligations.
Understanding Multi-Factor Authentication
To better understand multi-factor authentication, it's important to first understand what authentication is in the first place. At a high level, the process of authentication is used to verify that someone or something is who they claim to be. Typically, this involves providing some sort of proof in the form of credentials — such as a password, smart card, or a fingerprint. Given how important this process is in ensuring that your private information stays private, it's no surprise that providing higher levels of assurance around your authentication is a big focus in the industry right now. This is where multi-factor authentication comes in.
Multi-factor authentication, also known as MFA, is a security system that requires more than one method of authentication to verify the user's identity. The idea is that asking for additional evidence to prove who you are, drastically reduces the chance of a successful attack. This provided security, according to the National Institute of Standards and Technology, comes in the form of "increased resiliency against potential attacks" and "greater difficulty for an attacker to succeed." Not only that, but the use of multiple factors can provide additional assurance that the person who has been authenticated is the one actually trying to access the system. This can be really powerful — especially in preventing things like impersonation, where an attacker might use a stolen or lost device to assume the identity of a legitimate user.
So, in summary, multi-factor authentication helps in several ways. First, it provides increased security and makes it harder for attackers to gain access. And second, it provides additional assurance that the person who has been authenticated is the one actually trying to access the system.
Role-Based Access Control
First, let's understand what role-based access control (RBAC) is. As opposed to user-based access control where individual users have to be given their permissions to various resources within the system, RBAC is used to regulate the permissions of users in the system. This is a way of managing system access as changing user roles can be quite time-consuming and inefficient for system administrators. With RBAC, it is much easier to manage different users' permissions as they are associated with a particular role, and this role is then assigned the necessary permissions for it to perform its respective tasks. This set of assigned permissions to the role will be all that is needed for any user who is associated with that role to perform their job.
There are several different types of access control such as mandatory access control (MAC) and discretionary access control (DAC). However, the matter of which is better can become a hotly debated topic within the field of computer security. The use of role-based access control over other types of access control is a widely accepted approach for reasons such as "method more intuitive for privileged users" and "simplifies the security administrators' day-to-day work and reducing the likelihood of employee errors provoking deliberate or accidental insider attacks."
There are often three primary rules to follow to claim conformance to role-based access control standards. These are: "a subject can execute no more than one role at a time," "the role authorization of a subject can only be changed (i.e. added or deleted) by the holder of the role," and "the role authorization of a subject cannot be changed while the subject is in a session that is using that role."
Benefits of Role-Based Multi-Factor Authentication
When it comes to cyber security, access privileges are a key point of vulnerability. Those with higher clearance are the targets of cyber-attacks, as a successful breach into their account would yield much more data than that of a standard user. In response to this, many security professionals advocate for a method of access control known as role-based access control, in which employees are only granted access to the resources and information necessary for them to complete their current tasks. This lends itself well to the technical aspect of cyber security.
By using this system in tandem with multi-factor authentication, a practice that requires two or more pieces of evidence to prove identity, security professionals can ensure that the access they are trying to protect is truly valid. One of the greatest attributes of role-based multi-factor authentication is its adaptability to different scenarios and levels of security. As the specific roles and clearance of employees vary from company to company, it is important to be able to tailor the level of security to accommodate different risk levels.
With role-based access control, accounts can be categorized into different roles, each with its various levels of access. For instance, a junior employee might be restricted to general databases and applications, whereas an IT professional would have access to the more secure and private areas of the network. In the event of a breach, implementing role-based multi-factor authentication can greatly decrease the level of damage a cyber-attacker can inflict.
By compartmentalizing network access to only approved personnel, the number of systems and the amount of sensitive data that can be compromised is minimized. From an IT professional's perspective, this not only means that the clean-up and repair from a breach are less extensive, but it also reduces the risk of larger legal consequences when assessing cyber-attacks that involve potential data regulation violations.
Implementing Role-Based Multi-Factor Authentication
The process of implementing role-based multi-factor authentication varies in complexity depending on the specific resources and environments an organization is trying to protect. However, regardless of the resources you are trying to protect, the overall process typically follows a series of high-level steps.
The first step is to start by enabling multi-factor authentication for privileged accounts. This includes, at a minimum, accounts with administrative access and also includes power users with the ability to modify critical data. Multi-factor should be enforced for all attempts to log in to these accounts, either via the console or via remote access. This is often performed by drilling down and selecting privilege and user roles first, before moving on to adding and enabling security procedures.
For each role that will have an associated enforcement policy, you will need to select the role from the list of roles. Then say, as an example, click properties, click on the security settings tab, and then click the add button next to 'existing roles for this security policy'. Once the configuration is done the most practical tasks often involve the enrollment of existing users associating users with the different roles and setting up and configuring initial authentication methods for a new role-based deployment.
Of course, the root of trust vis-a-vis the identity provider is essential, and steps must be taken to ensure this part of the security model is well-designed. Finally, the continuous testing phase should not be overlooked. As with all cybersecurity projects, the implementation of multi-factor authentication has to be tested, validated, and maintained to ensure effectiveness. This includes ensuring that the way role membership is calculated and verified to ensure that users exercise the principle of least privilege is maintained. Second opinions and even formal cyber pen testing can help to validate that a role-based multi-factor deployment has been implemented correctly. Such formal testing will demonstrate to business leaders and auditors that the control has been operationally effective and give confidence that the security practice is fit for purpose.
With the rise of cloud computing and digital services, implementing strong access controls is integral in safeguarding both user and business-critical information. Multi-factor authentication is a key 'building block' control in this field and utilizing a role-based application can provide granularity over which accounts are enforced with multi-factor and under what context. This not only assists in ensuring a robust security model is maintained but also helps to streamline end user's interactions with multiple systems. It is clear that industry professionals must ensure that resources can be accessed by establishing different levels of security. In particular, as technology is developing to become more sophisticated, greater attention is required on the digital services processes. All in all, the move from traditional, 'first-factor' authentication to multi-factor authentication is a necessary step in enhancing security measures.
We Provide consulting, implementation, and management services on DevOps, DevSecOps, DataOps, Cloud, Automated Ops, Microservices, Infrastructure, and Security
Services offered by us: https://www.zippyops.com/services
Our Products: https://www.zippyops.com/products
Our Solutions: https://www.zippyops.com/solutions
For Demo, videos check out YouTube Playlist: https://www.youtube.com/watch?v=4FYvPooN_Tg&list=PLCJ3JpanNyCfXlHahZhYgJH9-rV6ouPro
If this seems interesting, please email us at [email protected] for a call.
Recent Comments
No comments
Leave a Comment
We will be happy to hear what you think about this post