Top 3 OWASP Vulnerabilities and How to Deal With Them
Each cyber vulnerability has its own way of solution. Find out more about the top 3 OWASP vulnerabilities, issues, examples that might arise, and how to deal with them.
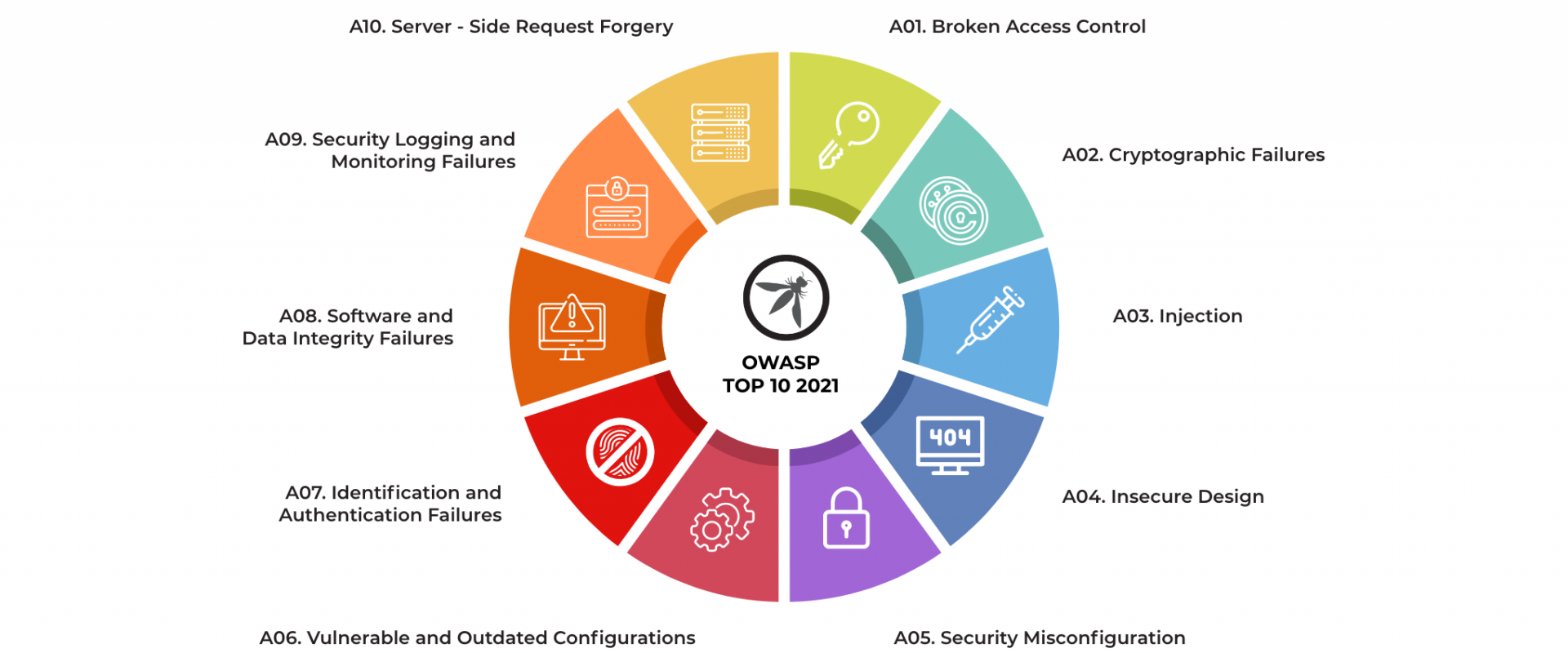
As you probably already know, Open Web Application Security Project addresses many threats and vulnerabilities in the cyber security environment. In order to carry out its purpose, OWASP offers forums all around the world as well as an online library stocked with books and materials for education. Basically, they’ve created a list of vulnerabilities that are worth your time taking care of. This list includes lots of threads, but all around the web, you can easily find the top 10 of them, including Broken Access Control, Critical Data Disclosure, Injection attacks, Broken Authentication, XML External Entities Injection, Cross-Site Scripting, Incorrect Security Configuration, Insecure Deserialization, Insufficient Logging, and Monitoring, as well as Using Components with Known Vulnerabilities.
Each cyber vulnerability has its own way of solution. So, I’ve decided to overview the top 3 vulnerabilities mentioned above since they are the most widespread. Let’s break them down by examples, descriptions, and options to prevent.
Broken Access Control
Attackers frequently employ weak access control to get around security measures and obtain sensitive data as well as unlawful access (including access to administrator privileges).
When creating apps, you have a variety of access control models to select from. To reduce safety concerns, the chosen model should be maintained throughout development and testing. When access permissions are incorrectly defined, it leads to broken access control, which enables attackers to access, edit, or delete data, files, and accounts to which they shouldn't have access.
What Issues Can Arise?
- Insecure IDs: We typically use a unique ID when searching for something in a database. However, if the web server is configured incorrectly, it may provide the user with requested information even though they are not permitted to access it.
- Forced surfing: Forced browsing occurs when a user tries to access resources that are still accessible but are not referenced by the program.
- Directory exploration: The server may anticipate a filename as a request argument when a website keeps data in many files.
- Client-side caching: Browsers save websites in their cache so that they load more quickly the next time a user accesses them. If numerous people use the same computer, this can be a problem. Developers must restrict browsers from caching sensitive information.
How to Prevent Broken Access Control?
- The default should be refused, with the exception of public resources.
- Execute access control mechanisms and process them across the entire program. Don't forget to use Cross-Origin Resource Sharing as little as possible.
- Model access limitations should ensure record ownership rather than enabling the user to create, read, update, or remove any records.
- Application business bounds need to be constrained by domain models.
- Eliminate any unnecessary services from your server.
- Record access control errors and alert administrators as necessary.
- If possible, use multi-factor authentication for all access points.
- Eliminate pointless accounts. Terminate a user's account if it is no longer required.
Critical Data Disclosure (Sensitive Data Exposure)
Information disclosure or information leaking typically happens when a website or app unintentionally shares sensitive information with people who are not authorized to read it or access it. The main cause of the danger of vital data leak is the use of inadequate encryption algorithms, insecure password storage techniques, lack of encryption, or the use of unreliable methods for generating and storing keys. Additionally, even when it's unnecessary, web application developers frequently store sensitive data.
What Issues Can Arise?
Examples that are often used include passwords, credit card information, medical details, and trade secrets. Data sent or saved in clear text or utilizing cryptographic methods like MD5 or SHA-1 are the two situations where such errors are most likely to occur.
Any data that may be exploited by hackers to access systems steal identities or commit other cybercrimes should be sent and kept using encryption.
How to Prevent Cryptographic Failures?
- To secure the data sent by the website, use the Secure Sockets Layer certificate.
- Always identify and categorize the data that is sensitive in accordance with the regulations and privacy laws.
- Remove any data that does not need to be kept right away.
- Make sure sensitive data is encrypted at rest if you want to store any.
- Implement sound key management.
- Make sure you use security protocols like TLS and SSL to encrypt any data while it is in transit.
- You may use HTTP Strict Transport Security to easily impose encryption on your application (HSTS).
- Don't cache private information.
- Always use several encryption techniques when storing passwords.
Injection Attacks
The main goal of an injection attack is to introduce SQL, NoSQL, OS, and LDAP into the application. Due to a lack of input validation and data sanitization, which might directly expose input into the query, injection happens when data is entered into a program from an untrusted source.
Since practically every website has this injection vulnerability, it is clear how serious it is since everything that accepts parameters as input is susceptible to injection.
What Issues Can Arise?
By including malicious data as part of a command or query, an attacker can execute unauthorized instructions or obtain access to confidential information. This typically occurs when a website neglects to apply parameterization, filter, validate, or sanitize user input.
The huge attack surface of injection vulnerabilities makes them extremely terrifying (especially for XSS and SQL Injection vulnerabilities). But, there are several trustworthy tools that are readily accessible for free that enable even novice attackers to automatically exploit these vulnerabilities.
How to Prevent Injection Attacks?
- You must keep the data separate from the instructions and queries in order to prevent SQL injection types.
- Bypass any interpreters or third-party procedures, and check the user's data directly.
- It is worthwhile to think about switching to object-relational mapping (ORM) techniques.
- Your defense against an injection assault may benefit greatly from the positive validation.
- Apply input sanitization and validation.
- Make certain that all user input is being escaped.
Summing Up
Of course, this is just a high-level overview of the top 3 OWASP vulnerabilities and actions to prevent related issues from expanding. But, the more deep analysis of how to deal with such threats might require additional code usage, and in this case, it’s better to involve some technical experts from your side. Nevertheless, I would be happy to hear your ways of solving such issues in the comments section.
We Provide consulting, implementation, and management services on DevOps, DevSecOps, Cloud, Automated Ops, Microservices, Infrastructure, and Security
Services offered by us: https://www.zippyops.com/services
Our Products: https://www.zippyops.com/products
Our Solutions: https://www.zippyops.com/solutions
For Demo, videos check out YouTube Playlist: https://www.youtube.com/watch?v=4FYvPooN_Tg&list=PLCJ3JpanNyCfXlHahZhYgJH9-rV6ouPro
If this seems interesting, please email us at [email protected] for a call.
Relevant blogs:
All the Questions You Were Afraid to Ask About SBOM
A Security Team’s Most Critical Skill? No-Code Automation
Container vs. VM Security: Which Is Better?
Where Does Cybersecurity Go From Here?
Recent Comments
No comments
Leave a Comment
We will be happy to hear what you think about this post