10 Effective Strategies To Safeguard Your IoT Network From Threats

The security of IoT networks is a challenge that needs to be addressed at a global scale. This blog will uncover some risks associated with IoT network security.
IoT is one of the leading technologies in the world and has added a new level of comfort and convenience for people. Whether it is your home, office, or industry, IoT enables us to do work more quickly and precisely. However, when using IoT devices, various people often neglect the security aspect of IoT networks.
As we all know, IoT devices are smart and designed to gather our data all the time. This means your network if not secured, is vulnerable to hacks, thefts, and unauthorized access to your private information. Therefore, you must take adequate steps to prevent any lethal attacks on your IoT network and keep it safe.
So in this blog, we will discuss some vital risks surrounding your IoT network and how to safeguard the network from them. Let us begin!
Understanding the Security Risks Involved in IoT Networks
IoT networks contain more information on you than you can imagine. This information can be leveraged in multiple ways to know about your consumer behavior and even deduce personal information. Hence, it is essential to keep your IoT network secure at all times.
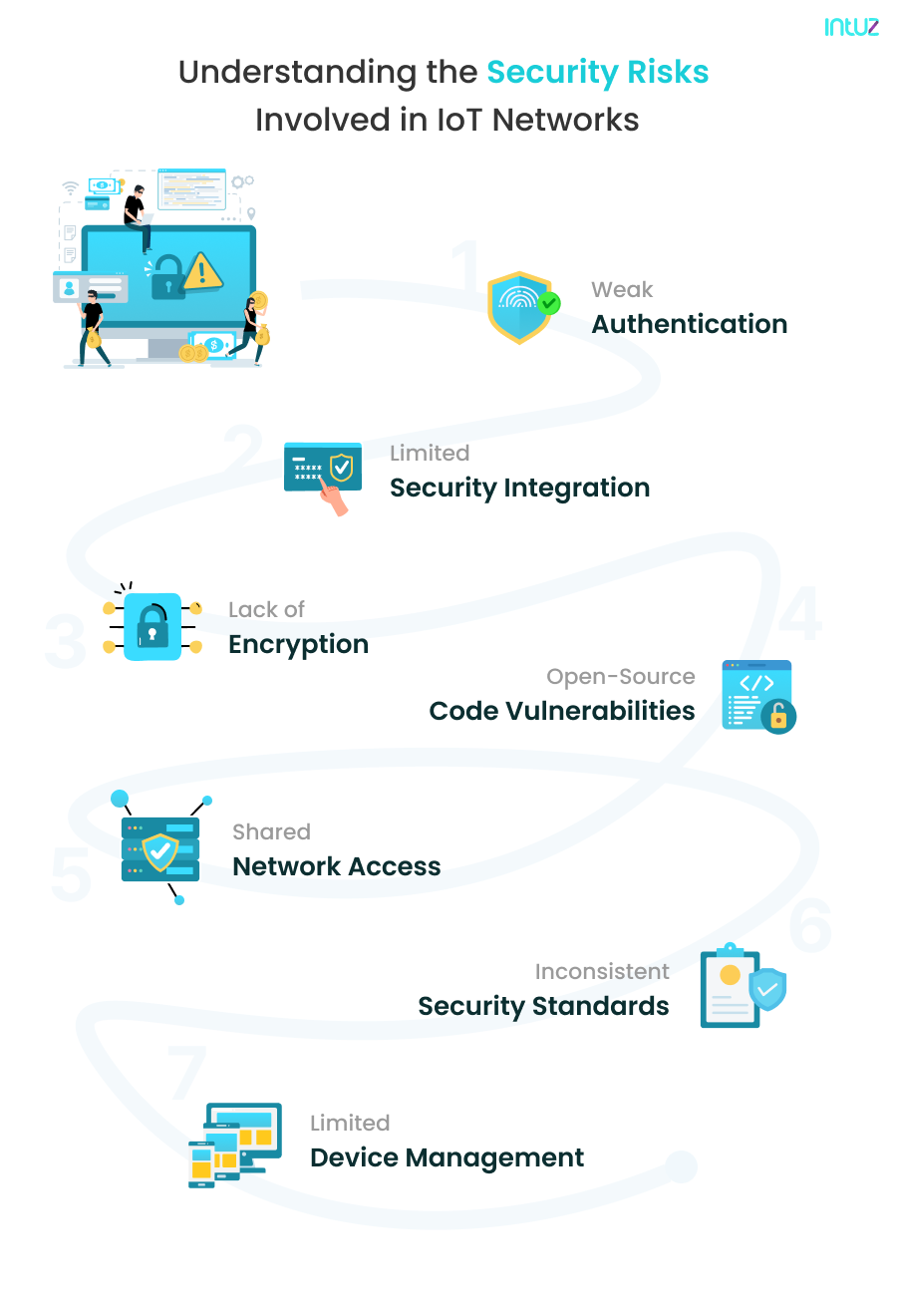
Security Risks That Pose a Threat to Your IoT Network
Weak Authentication
It is one of the most serious concerns for IoT security. Most IoT devices used daily have little, weak, or no authentication at all. This means you can access these devices and their data without actually authenticating yourself.
This can lead to various kinds of cyber attacks, such as intrusions, denial of service (DDoS) attacks, etc. Therefore, you must always protect your IoT network and devices with strong user-generated passwords.
Limited Security Integration
Another substantial challenge that poses a risk to IoT networks is the integration of all smart devices into secured IoT networks. There is a wide range of smart devices available today on the market. You can introduce any of these devices to your IoT network and enjoy their work.
However, all these devices come from different manufacturers and can not ensure the same security features on all of them. Hence, any unsecured smart device connected to your IoT network can be used to conduct a cyber attack.
Lack of Encryption
It is a common mistake made by a number of IoT users. The users lack integration of encryption methods in their networks while transmitting data. This means the network is totally open and accessible, and hackers can breach the network at any time and steal valuable information from it. Therefore, you must always practice encrypting your data while sending it through an open network.
Open-Source Code Vulnerabilities
Today we live in a world of open-source programming. Most applications, devices, and software use open-source code for their creation which is accessible to everyone.
Unfortunately, most open-source software usually consists of numerous bugs and vulnerabilities. Hackers can use these vulnerabilities in the applications to access your network and steal information from it.
Shared Network Access
All IoT devices are generally connected to the same network to make the transition of data and the working of IoT devices seamless. However, this shared network access often becomes the reason for cyber attacks, as any device can easily approach it.
To solve this challenge, different networks can either use a distinct network for them or use a firewall that can isolate the attack at the device level only.
Inconsistent Security Standards
IoT does not have any universal security standards that can be applied to all devices and networks. As the nature of the IoT ecosystem is dynamic, building specific IoT standards for all industries and devices is not possible.
Hence, manufacturers themselves have to create their own protocols and guidelines and embed those features into their devices or software to enhance the security of their IoT devices.
Limited Device Management
Device management is one of the keys to eliminating security risks from IoT devices and networks. Devices, when they get compromised, tend to consume data differently. Their behavior can be observed and detected to determine if they are working appropriately or not.
So, users must have visibility and control over their devices to shut them off remotely if the device shows suspicious behavior.
10 Actionable Steps To Take To Secure Your IoT Network
Here are some useful tips and ways to secure your IoT network and prevent it from unauthorized access and cyberattacks.
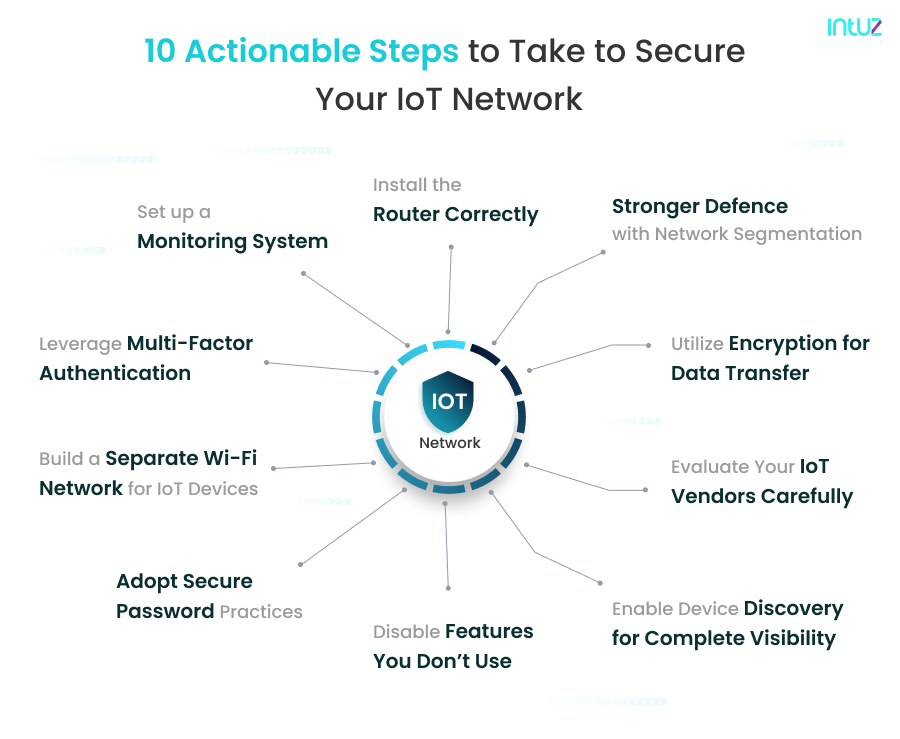
Leverage Multi-Factor Authentication
MFA is undoubtedly one of the best techniques to safeguard your IoT network. It uses more than two pieces of evidence in its authentication process before allowing anyone to access the network.
The authentication can either be code based or physical. Physical authentication involves using a USB stick to access a network or device. MFA ensures that your network stays secure and free from undesired cyberattacks.
Set up a Monitoring System
Your IoT network must always be in a state of monitoring, especially when multiple IoT devices are attached to it. A monitoring system tracks your device's health and functioning and alerts the admin on the occurrence of any suspicious activity.
The activity may be unauthorized access to a network, an unusual data flow, a connection to a new network, etc. Keeping your monitoring system up and running is indeed a good way to keep your sensitive information away from hackers.
Install the Router Correctly
Your router is the gateway to your IoT network. Hence, it is vital to keep your router secured and away from threats at all times. To do so, practice:
- Regularly changing the name of your router.
- Setting up a unique and strong password for the network.
- Use WPA-2 (one of the best encryption techniques) encryption to secure the network.
Keeping your router safe from unauthorized access is the best way to secure your IoT network.
Make Your Defense Stronger With Network Segmentation
Network Segmentation can be a viable solution for your IoT network security challenges. It is the process of segmenting an internal network into multiple layers or sub-networks. These networks are usually independent and can communicate with one another.
Above that, they are protected by a firewall, ensuring enhanced security for the network. Also, if a hacker manages to break into the network, they will only be able to gain access to that specific network, and data from other sub-networks would be protected.
Utilize Encryption for Data Transfer
Most hacks and breaches occur while data is being transferred from one point to another. Users need to pay more attention to the importance of securing data while it is in transit.
Hackers leverage this opportunity and attempt to steal the sensitive data of users. Therefore, you must always use encryption methods when sending out data to protect its integrity and keep it safe.
Build a Separate Wi-Fi Network for IoT Devices
Modern routers today can establish secondary networks if needed. You can avail of this feature and create a separate Wi-Fi network explicitly dedicated to IoT devices.
Use this network to manage your IoT devices and keep the network protected from hacks using encryption. It is a simple yet effective way of amplifying your IoT network security.
Adopt Secure Password Practices
Make sure your passwords aren’t ones to give away your network access. Passwords are a great way to keep your network out of the reach of others.
Hence, make sure to leverage good password practices and protect your IoT network. Here are some practices you can follow:
- Update your passwords every new month.
- Use strong passwords, including letters, numbers, and characters.
- Keep different passwords for different IoT devices.
These good password practices will ensure that your network is never infringed on because of a weak password.
Disable Features You Don’t Use
IoT devices give you the freedom to use them from anywhere on the planet. However, if you only use them from your home premises, it is better to disable those unrequired features.
Turning them off would ensure that no other entity than you access your devices, and they stay effective for only your use.
Enable Device Discovery for Complete Visibility
Eventually, all you got is to protect your devices from hacking. So, the first step in ensuring so is to generate a comprehensive list of all the IoT devices you use. Identify their manufacturer, model ID, serial number, hardware, software and firmware versions and note them in a document.
Next, analyze the risks associated with those devices to the network and add that information to your prepared document. Keeping this device discovery list updated and monitored will help you always stay secure from attacks.
Evaluate Your IoT Vendors Carefully
Lastly, make sure to evaluate the abilities of your IoT vendors. When choosing a vendor, ask them to provide a clear understanding of their accountability and liabilities. Also, learn about their experience and expertise in the field. It will help you get the best vendor and ensure security for your IoT network and devices.
Summing Up
IoT is an evolving technology that has yet to standardize itself. Hence, there are various security risks linked to IoT that users need to deal with themselves. However, following the given practices is enough to secure your IoT network.
We Provide consulting, implementation, and management services on DevOps, DevSecOps, DataOps, Cloud, Automated Ops, Microservices, Infrastructure, and Security
Services offered by us: https://www.zippyops.com/services
Our Products: https://www.zippyops.com/products
Our Solutions: https://www.zippyops.com/solutions
For Demo, videos check out YouTube Playlist: https://www.youtube.com/watch?v=4FYvPooN_Tg&list=PLCJ3JpanNyCfXlHahZhYgJH9-rV6ouPro
If this seems interesting, please email us at [email protected] for a call.
Relevant Blogs:
The Effect of Data Storage Strategy on PostgreSQL Performance
Understanding Data Compaction in 3 Minutes
CPU vs. GPU Intensive Applications
Automating Data Quality Check in Data Pipelines
Recent Comments
No comments
Leave a Comment
We will be happy to hear what you think about this post