Security Challenges for Microservice Applications in Multi-Cloud Environments
Multi-cloud strategies bring new security concerns. As a result, organizations need to address them at every stage of their security measures.
As more organizations expand their cloud strategy into a mix of private cloud, public cloud, on-prem data centers, and edge sites, thus embracing multi-cloud as part of their digital transformation initiatives, new security challenges emerge and must be considered at every stage of security initiatives.
Operating in the cloud offers multiple benefits, and any organization, whether public, private, or governmental, currently uses a cloud of some kind to accomplish at least part of its business functions.
According to data from the f5 2023 State of Application Strategy (SOAS) Report, 85 percent of organizations operate applications with multiple architectures and deploy them across distributed environments. Operating in the cloud comes with several security challenges, and the complexity increases further in a multi-cloud environment, with the need to connect applications running in different environments with potentially different sets of security policies, governance, and compliance requirements.
On top of the security and complexity challenge introduced by the use of multi-cloud, monolithic applications are also being progressively abandoned in favor of microservices that offer greater flexibility and easy provisioning and de-provisioning. This adds to the already existing challenges, with an expended cyberattack surface, reduced end-to-end visibility into the application's health and performance, and an increase in operational complexity.
Challenges Caused by Differences in Architectural Design
Differences presented in each environment make it more difficult to apply a consistent security policy across environments. Requirements for workloads security, applications security, and API security are not necessarily harmonized in the private cloud, public cloud, or edge computing environments.
Harmonizing security policies across different clouds remains a challenge for many organizations, with a greater impact on monitoring and visibility.
Using a distributed cloud technology, sometimes referred to as super-cloud, is increasingly gaining ground.
As described by researchers from Cornwell University, "Supercloud is a cloud architecture that enables application migration as a service across different availability zones or cloud providers. The Supercloud provides interfaces to allocate, migrate, and terminate resources such as virtual machines and storage and presents a homogeneous network to tie these resources together. The Supercloud can span across all major public cloud providers, such as Amazon EC2, Microsoft Azure, Google Compute Engine, Rackspace, etc., as well as private clouds. "
Cloud Security Model
Public cloud providers use a shared security model, in which the provider is responsible for the security "of the cloud," and the consumer is responsible for the security "in the cloud."
This model implies that the cloud provider is responsible for the platform's security, including hardware and all hypervisor components. The customer is responsible for their own security policies and governance model and setting the right controls for their applications, data, and API protection. This also includes configuration management for DDOS protection, Web Application Firewall (WAF), guest operating systems, and guest data storage management.
In this model, the challenge for data, applications, API, and workload security rest on the customer's shoulders. The learning curve that is required to close the knowledge gap between private, public, hybrid, and multi-cloud may quickly become the cause of potential weak points. A recent study by Gartner estimates that by 2025, 99% of cloud security failures will be customer's fault. This can be attributed to difficulties in enforcing security policies across different environments and the inability to integrate cloud governance, risk management, and monitoring into existing information security life cycle approaches.
Challenges Posed by the Transition From Monolithic to Microservice Application Service and Data
Traditionally, Network firewalls, Intrusion detection systems (IDS), and Web application firewalls have been used to provide security to enterprise infrastructure, with different levels of success; however, adapting this defense mechanism to a microservice architecture where new applications can be provisioned or de-provisioned dynamically is one of the biggest challenged faced by organizations. With the complexity added by microservice architecture, it becomes more difficult to apply a consistent enterprise security policy for new workloads and applications.
Most tasks need to be automated and cloud-native tools such as Kubernetes clustering need to be implemented for automated deployment and orchestration of new applications and enforcement of security policies for new services.
Properly running cloud-native tools such as Kubernetes requires trained cloud and security professionals, and this itself is another important challenge faced by organizations.
Challenges Posed by Skills Gap in Cloud and Information Security Professionals
Most organizations are adopting a multi-cloud-by-default in their technology investment strategies, and investment in cloud technology has seen a 49% increase in 2023 from 2017. Gartner also estimates that IT spending will increase to $4.6 trillion in 2023, but this increase in IT investment faces an important challenge with a shortage of trained professionals to manage, operate and secure the ever-complex infrastructure.
Multi-cloud, by default, is becoming an obvious IT strategy for organizations. However, most professionals don't have the cloud expertise needed to manage these modern solutions that span public cloud, private cloud, on-premise data centers, and edge computing workloads. As we stated earlier, multi-cloud environments create a complex cybersecurity environment that most organizations aren't prepared to handle.
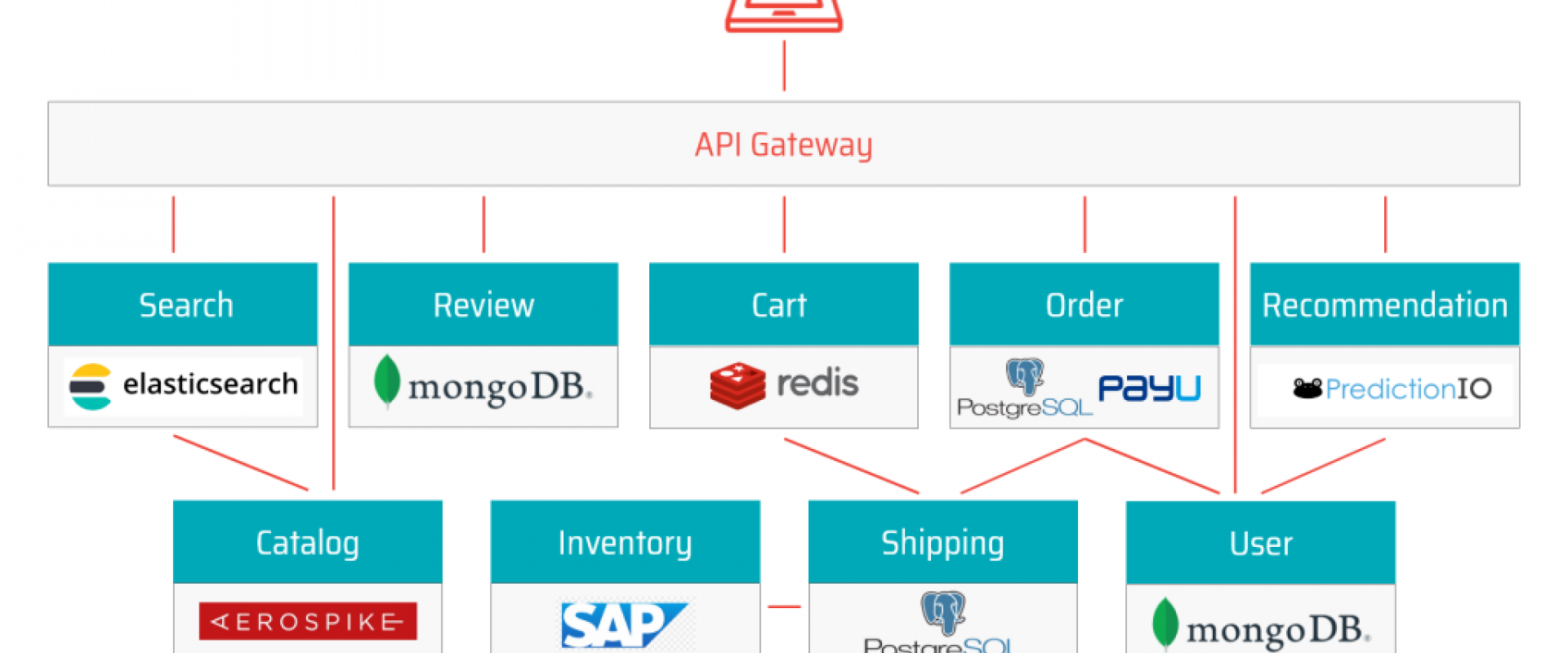
The two largest technology skills gaps are cybersecurity and cloud computing. However, despite increased Investments in technology, particularly in cloud technologies, organizations have not invested in upskilling their staff at a rate to close the technology skills gap.
One solution to closing the skills gap is for organizations to invest in training and education for existing employees by providing access to learning platforms as well as sandbox environments where they can practice with cloud and security technologies in order to be better prepared for the production environment and real-life cloud and security challenges.
The following figure produced by a Pluralsight survey shows a skill gap by sector.
Security as a Service (SECaaS) To the Rescue
Moving to a public cloud provides the advantage of not having to worry about the security of the physical infrastructure (The security of the cloud), but the infrastructure security remains the responsibility of the organization in a private cloud within the multi-cloud model. Also, applications are still vulnerable to the usual threats, whether in a public or private cloud. Ransomware attacks, DDOS attacks against application and API endpoints, Zero-day exploits of previously unknown vulnerabilities, credential stuffing, or replay attacks remain a challenge, and the number of attacks is increasing. There's a breach every 39 seconds and a ransomware attack every 14 seconds, according to Cybersecurity Ventures.
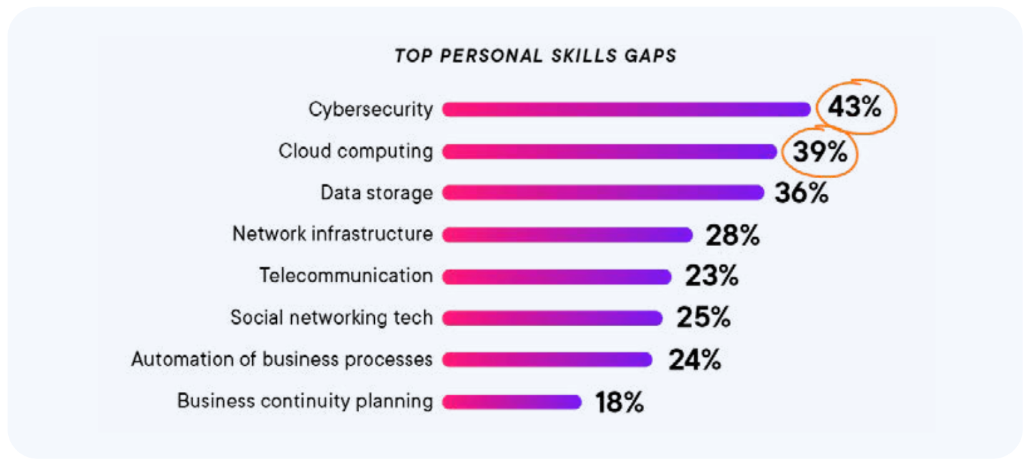
In order to maintain the lead in the race against cybercriminals, organizations are turning to Security as a service (SECaaS) providers to help keep their digital assets safe, and the reasons for this, according to data from f5 2023 State of Application Strategy (SOAS) Report is because of the need of speed and the lack internal skills, as shown in the following graph.
Conclusion
As multi-cloud-by-default takes the central stage in IT strategy for most organizations, the complexity that is introduced by this new approach brings increased security challenges. Cloud infrastructures are automated by cloud-native tools such as Kubernetes for the deployment and orchestration of workloads and applications. However, implementing this strategy in a secure way requires skilled professionals, but the availability of skilled professionals is not growing at the rate needed to close the skill gap that exists in the cloud and security space.
There is a need for organizations to invest more in upskilling their existing employees in order to help mitigate the skill gap challenge. Other organizations are turning to Security as a service (SECaaS) providers to keep up with the speed needed to patch vulnerabilities before they are exploited by bad actors.
We Provide consulting, implementation, and management services on DevOps, DevSecOps, DataOps, Cloud, Automated Ops, Microservices, Infrastructure, and Security
Services offered by us: https://www.zippyops.com/services
Our Products: https://www.zippyops.com/products
Our Solutions: https://www.zippyops.com/solutions
For Demo, videos check out YouTube Playlist: https://www.youtube.com/watch?v=4FYvPooN_Tg&list=PLCJ3JpanNyCfXlHahZhYgJH9-rV6ouPro
If this seems interesting, please email us at [email protected] for a call.
Recent Comments
No comments
Leave a Comment
We will be happy to hear what you think about this post