The Future of Incident Response: SOAR's Impact on Cybersecurity Defense

Discover how SOAR is revolutionizing incident response strategies, safeguarding organizations from relentless cyber threats. Stay ahead of the curve.
In February 2024, a slew of notable entities fell victim to cybercrime, ranging from UnitedHealth and the personal accounts of Axie Infinity's co-founder to Hewlett Packard Enterprise, AnyDesk, and various French healthcare payment service providers like Viamedis and Almerys. Even critical institutions such as Integris Health, Schneider Electric, Lurie Children's Hospital, and a California union, alongside infrastructure like Trans-Northern Pipelines, were not spared from these attacks.
These incidents underscore a stark reality: in today's digital landscape, no organization, regardless of its size or stature, is impassable to cyber threats. The past three months alone have witnessed a surge in cyber and ransomware attacks, showcasing the indiscriminate nature of such malicious activities.
It's evident that relying solely on preventive measures is insufficient in safeguarding against the evolving tactics of advanced hackers. What's crucial is a robust Cyber Incident Response strategy, capable of swiftly and effectively mitigating the impact of an attack when defenses are breached.
In the turbulent realm of cybersecurity, the ability to swiftly rebound from a sophisticated cybercrime is paramount to maintaining operational continuity. A well-crafted Cyber Security Incident Response plan is the cornerstone of resilience, ensuring minimal disruption to your operations even in the face of relentless attacks. Moreover, it acts as a bulwark against substantial financial losses and potential legal ramifications, shielding your organization from the fallout of breaches and compliance breaches.
Implementing a robust cybersecurity incident response plan is central to effective cyber resilience. However, it's not merely about having a plan in place; it's about refining and fortifying it through meticulous rehearsal and scrutiny. Cyber crisis tabletop exercises serve as invaluable tools for identifying and addressing any gaps or vulnerabilities in your response strategy, ensuring readiness to combat cyber threats with precision and agility.
Now, let's delve into the concept of SOAR (security orchestration, automation, and response), a transformative approach to cybersecurity. SOAR represents a suite of seamlessly integrated software programs designed to empower organizations in their cybersecurity endeavors. By leveraging SOAR, entities can effortlessly gather comprehensive data on cybersecurity threats while orchestrating swift and targeted responses with minimal human intervention.
How Does SOAR Work?
At its core, a SOAR platform comprises three key components: security orchestration, automation, and response. These elements work synergistically to enhance the efficiency of physical and digital security operations, enabling organizations to tackle evolving threats with unparalleled speed and efficacy proactively.
Elements of SOAR
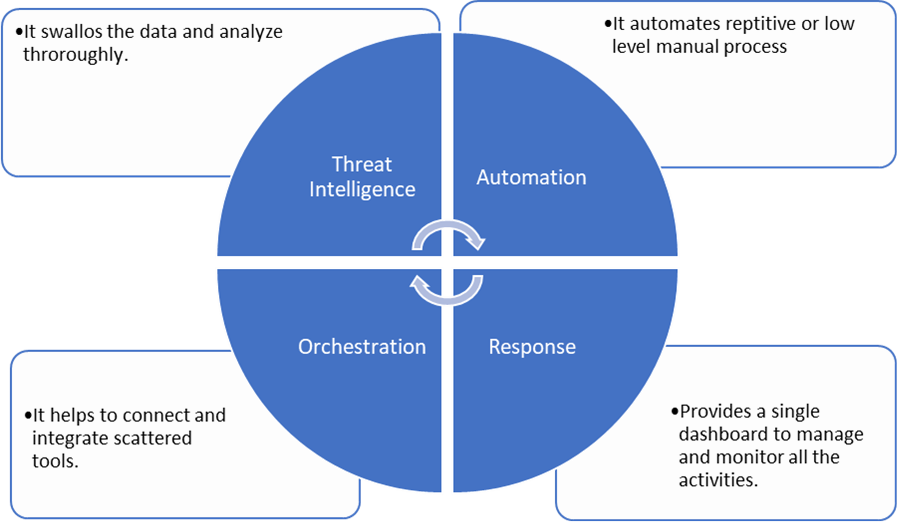
As you embark on refining your cybersecurity incident response plan and ensuring its regular rehearsal, the realm of automation and orchestration emerges as a beacon of efficiency and effectiveness. These indispensable tools not only alleviate the burden on security analysts but also fortify the organization's incident response capabilities.
Automation within cyber security incident response heralds a paradigm shift, where technology takes the reins in executing repetitive and time-consuming tasks autonomously. From threat identification to incident categorization based on severity and the initiation of predefined response actions, automation streamlines the entire process.
The advantages of automation in Cybersecurity Incident Response are multifaceted:
- Efficiency and speed: By eliminating the need for human intervention in identifying anomalies and incidents, automation drastically reduces the time required to detect and respond to threats. This swift response capability is instrumental in mitigating the potential damage inflicted by cyber attacks, especially when handling a large volume of security events in real-time.
- Consistency and accuracy: Automated incident response platforms provide a consistent and reliable approach to handling incidents, mitigating the risk of human error. By automating routine tasks, the likelihood of mistakes stemming from fatigue or oversight is minimized, ensuring the accuracy and reliability of response actions.
- Quick implementation: Automation allows for the immediate implementation of predefined response strategies, ensuring a swift and standardized response to cyber attacks. While human intervention may be necessary for specific decisions and targeted response steps, automation saves valuable time and resources in handling generic incidents.
How Orchestration Is Transforming Cyber Incident Response Today?
Transitioning to orchestration in incident response, it embodies the seamless coordination of diverse tools and processes to streamline cyber incident response efforts. By fostering better communication and collaboration among different security teams and tools, orchestration optimizes resource utilization and enables a more strategic approach to incident management.
Benefits abound:
- Enhanced collaboration: Facilitating fluid communication among security teams and tools, orchestration fosters synergy in tackling incidents.
- Optimized resource utilization: Maximizing the efficacy of cybersecurity resources, orchestration ensures the right tools are deployed for each task, notably within SOAR frameworks.
- Strategic incident management: Guiding response efforts in alignment with organizational policies, orchestration empowers Security Operations Center (SOC) teams to focus on high-value tasks while automated workflows handle routine operations.
The integration of automation and orchestration is pivotal in fortifying cyber defense mechanisms against increasingly sophisticated cyber threats. Businesses can enhance decision-making processes and strengthen their overall cyber defense posture by automating detection and orchestrating a swift response.
Final Words
The amalgamation of automation and orchestration revolutionizes cybersecurity incident response, paving the way for streamlined processes, enhanced operational efficiencies, and proactive management of organizational cyber resilience. By liberating cybersecurity experts from labor-intensive tasks, these technologies empower them to focus on continually improving response capabilities and bolstering cyber defense strategies.
We Provide consulting, implementation, and management services on DevOps, DevSecOps, DataOps, Cloud, Automated Ops, Microservices, Infrastructure, and Security
Services offered by us: https://www.zippyops.com/services
Our Products: https://www.zippyops.com/products
Our Solutions: https://www.zippyops.com/solutions
For Demo, videos check out YouTube Playlist: https://www.youtube.com/watch?v=4FYvPooN_Tg&list=PLCJ3JpanNyCfXlHahZhYgJH9-rV6ouPro
If this seems interesting, please email us at sales@zippyops.com for a call.
Recent Comments
No comments
Leave a Comment
We will be happy to hear what you think about this post